What is an Information Security Management System?
An Information Security Management System or ‘ISMS’ is a way for your organisation to mitigate Risk. An ISMS is essentially a structured framework of polices and controls that systematically manage information security risk. While every business is exposed to privacy and security threats, it is essential that businesses ensure their processes and policies reduce this risk where possible. This is achieved through an Information Security Management System focused on Risk Assessment, Risk Control and Risk Management.
An ISMS requires an organisation to fully develop an Information Security Policy which will affirm their commitment to Information Security. Following this you must also identify your security risks and understand both the internal and external influences and external parties relevant to Information Security. A Statement of Applicability must also be developed, assessing identified risks and their treatment. Procedures are then be reviewed and developed to provide information security guidance and instruction, including ways to monitor objectives and performance.
The Plan, Do, Check, Act Cycle forms a large part of any management system including an ISMS, pushing continual improvement and review of information security from every level of the organisation. An effective Management Manual, covering relevant information security Standards or legislation and regular Audits of the system will also form an important part of a value adding Information Security Management System.
What are the Benefits of an Information Security Management System?
Implementing an Information Security Management System can increase your organisations resilience to cyber-attacks through mitigating information security risks. An ISMS will bring an increased awareness of potential and actual information security threats to an organisation, combined with a risk treatment plan with effective controls, the resulting risk will be reduced, ensuring your business has a quick and effective response to undesirable information security events.
An ISMS will showcase your due diligence in respect of information security risks, highlighting your commitment to meet regulatory and client requirements. This is in addition to meeting International Industry best practice Standards. By increasing your resilience to cyber-attacks, you can reduce the risk of information loss, disclosure and even fraud and ensure you can quickly detect data leakage issues and respond efficiently and effectively, reducing your overall costs.
An ISMS will benefit your company by assisting to protect all forms of information, from cloud-based and paper-based records to intellectual property. Through effective implementation you can also be sure that your employees have an awareness of risk and the knowledge and competence to identify, treat, manage and review information security risks.
Implementing an Information Security Management System can assist your business to:
- identify information security risk
- evaluate Information security risk
- treat information risk
- reduce costs
- improve efficiency
- increase employee engagement
- protect data and records
- qualify for government tenders and defence contracts
- competitive edge.
What is ISO 27001?
ISO 27001 is the International Standard for Information Security Management Systems. While not a prescriptive document, ISO 27001:2022 sets out the requirements for establishing, implementing and maintaining an information security management system that will continually improve.
The Standard can be applied to any organisation, in any industry, of any size and includes the requirements to assess and treat information security risk through a documented Statement of Applicability.
The Standard looks at the context of the organisation, understanding relevant internal and external issues and interested parties relevant to its information security system. The scope of the system must also be established considering dependencies between activities performed by the business and those performed by other organisations.
In addition to demonstrated leadership and commitment to the Information Security Management, the Standard also requires a clear and robust information security policy and the communication of relevant roles and responsibilities. The Standard states that the organisation must establish information security objectives which are relevant and communicated at all levels of the company.
Information Security Planning must include actions to address information security risks and opportunities, including undertaking a risk assessment to identify and analyse relevant risks and a corresponding risk treatment plan to control the risk level. As part of ensuring there are the relevant resources to establish, implement and maintain the information security management system, the organisation must ensure relevant personnel are competent in their assigned roles and have an awareness of the policies and procedures that make up the information security system, and that all functions are communicating effectively.
A thorough and effective Document Control process is also an important part of ISO 27001, ensuring the creation, distribution and update of information security documentation is carried out in line with the Standards requirements.
The Standard requires the planning, implementation and control of information security processes and the ongoing review of risk assessments and associated treatment plans and the continual review of information security performance in respect of the company’s scope and context. Through Internal Audits, Management Review Meetings and non-conformance and corrective action monitoring, the Standard requires a continual cycle of improvement.
ISO 27001 also includes an Annex of Security Controls that are broken down by different categories, the Standard requires an organisation to review its risk assessments and select the applicable controls based on your requirements.
Why Certify Your ISMS to the ISO 27001 Standard?
A management system certified to ISO 27001 proves compliance with the International Best Practice Standard for Information Security which will not only mitigate the risk of cyber-attacks, but will also show stakeholders your commitment to protecting company and client data. By having documented policies and processes in place and an effective risk treatment plan, you can be sure you can mitigate risks and react quickly and efficiently if any information security events do occur.
One of the primary reasons to certify your management system to ISO 27001 is to help you avoid security threats, including external cyber break ins and internal cyber breaches. By implementing the requirements of the Standard, your organisations will have a strong information security framework focused on policy, procedures and competent people at all levels of the organisation. This will lower the risk of cyber threats and therefore protect your organisations reputation.
A certified ISO 27001 Management System will improve your organisations efficiency and ability to deal with information security change. By adopting a framework that is focused on planning, support, operation, and continual improvement at every level of the organisation, your business and key personnel will be able to adapt and grow with changing information security climates and unforeseen cyber events.
Developing and certifying your Information Security Management System to the ISO 27001 Standard can benefit your business and assist it to:
- prove compliance with International Best Practices
- protect your organisations data
- protect your Brand Image and reputation
- avoid costs from fines as a result of noncompliance with information security legislation
- improve your IP and data security
- adapt to the changing information security climate with ease and efficiency
- provide trust and confidence in your supply chain
- apply for tenders that require ISO 27001 certification
- give employees pride in the organisations efforts and trust in the management system
- improve efficiencies
- drive continual improvement.
How We Can Help With Your ISMS
At JLB, we understand that no two management systems are the same and our approach is to tailor your Information Security Management System to your organisations industry, size and security requirements. From an initial Gap Analysis reviewing your current management systems against the requirements of the International Standard, to the implementation of the policies and processes that will form your ISMS, JLB can consultant at every step of the way.
Our approach for the implementation of an information security management system will include curating a tailored security policy, facilitating a risk assessment and treatment plan, building a statement of applicability, taking into account the relevant information security controls, and developing an ISMS Manual and associated procedures. This is then delivered along with specific and relevant Information security objectives, a plan for performance monitoring including nonconformance monitoring and internal audits review and appropriate training to ensure stakeholders can competently carry out their information security responsibilities.
Once we have assisted you with implementing your Information Security Management System you can confidently apply for third part certification to the ISO 27001 standard with the knowledge that that system is prepared and ready for audit.
At JLB we know that continual improvement drives all effective management systems and as such we recognise that maintaining the system post implementation and certification is key to continued success and versatility throughout the lifecycle. Our consultants can assist to maintain your ISMS post certification to ensure ongoing compliance and continual improvement:
- review your current information security arrangements and ensure your business has addressed the basic requirements of an ISMS
- develop a Management Manual in your own terminology to reflect how your business addresses the requirements of ISO 27001, including the relevant roles and responsibilities required
- we then assist with the development of a Statement of Applicability to record the controls (security measures) from ISO 27001 Annex A (also in ISO 27002) that has been or will be implemented, including a justification for their inclusion/exclusion
- we then ensure the risk assessment methodology effectively includes information security criteria
- we train all relevant employees in the resultant ISMS
- we ensure all compliance obligations are identified and regularly monitored
- we train your Internal Audit Team and conduct the first internal audit
- we participate in the first management review meeting
- finally, we fully prepare you for 3rd party certification.
What to Expect When You Work with JLB
JLB knows that the strength of an Information Security Management System is based a thorough and detailed information security risk assessment in the first instance. Our consultants have the technical information, audit experience and industry knowledge to lead you through this process and ultimately add value to your management system.
Our longevity in the industry, expert knowledge and experience, along with our hands on approach to implementing management systems means you can be sure you’ll achieve third part certification first time round.
Let JLB add value to your organisation by implementing an Information Security Management System.
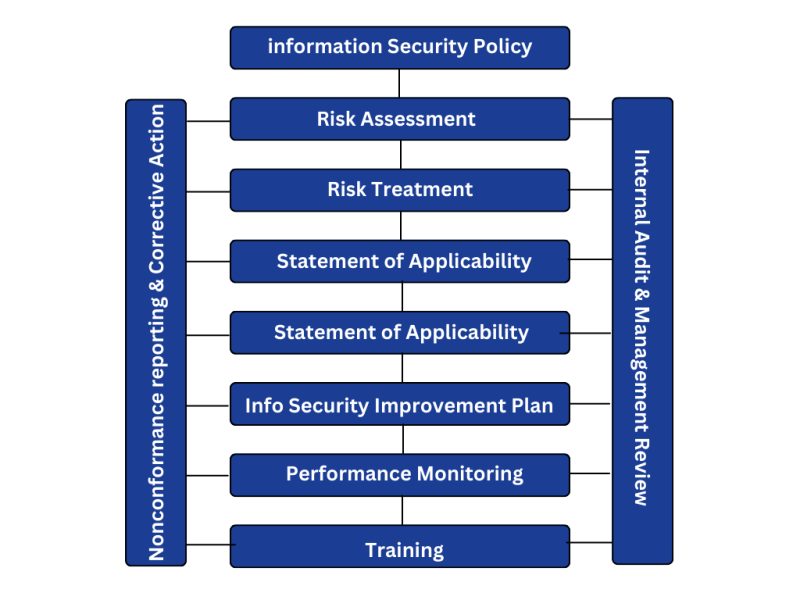
The Information Security Management System Process
JLB can assist at every step of the Information Security Management System process, from defining your information security objectives, to risk assessments and treatments, procedures and plans, performance monitoring, and training. The Information Security Process in the context of ISO 27001 revolves around a cycle of continual improvement. At the beginning of this cycle its integral to define your organisations information security scope and relevant objectives, this information is then documented and an information security policy created. The next step is to conduct a thorough risk assessment and associated risk treatment plan, with a statement of applicability and ISMS Manual and procedures to accompany these. Through training, nonconformance reporting, internal audits and management review meetings, all aspects of the systems are monitored for performance and the cycle of continual improvement continues.
Learn about the international standard and what achieving ISO 27001 can do for your business
Our experienced, committed and dedicated team tailors a program to suit your individual needs
Third party assessment to gain certification for your Information Security Management System
JLB is available to maintain your ISMS to ensure compliance and continual improvement
Information Security Management System Documentation
We work with you to ensure that your ISMS documentation meets the requirements of the ISO 27001 Standard and includes all the documents you need to comply. This includes verifying that your Information Security Policy Statement, Statement of Applicability, ISMS Management Manual, and documented procedures, information security objectives and targets, and non-conformance and corrective action reporting, are formulated in line with the ISO 27001 Standard.
Why Choose JLB for your ISO 27001 Information Security Management System development?
Experienced Information Security Consultants
Tailored ISMS implementation
Maintenance of your ISMS
- ISMS Training
Risk Assessment Software
- Integration with other Standards.
JLB is a leading Australian management systems consultancy with over 30 years experience and expertise in helping businesses develop, implement and achieve ISO certifications.
Talk to us today to find out how an ISO 27001:2022 certified Information Security Management System can help your business manage information security.